I summarize the permissions you need on the object depending on the parameter you specify on the ktpass command:. In corporate scenarios it is common to have non MSFT native tools that requires keytab files for implementing its Kerberos authentication mechanisms. I know that those parameters -SetUPN or -SetPass look counter intuitive since they do the opposite of what it suggests. The following code shows the functions that are available when you enter the ktpass -? Several Password vault systems allows this. To ensure the restored objects will win all replication conflicts, the attribute version of all the attributes of the objects in the scope of an authoritative restore will by default be incremented by A Kerberos keytab file contains a list of keys that are analogous to user passwords. 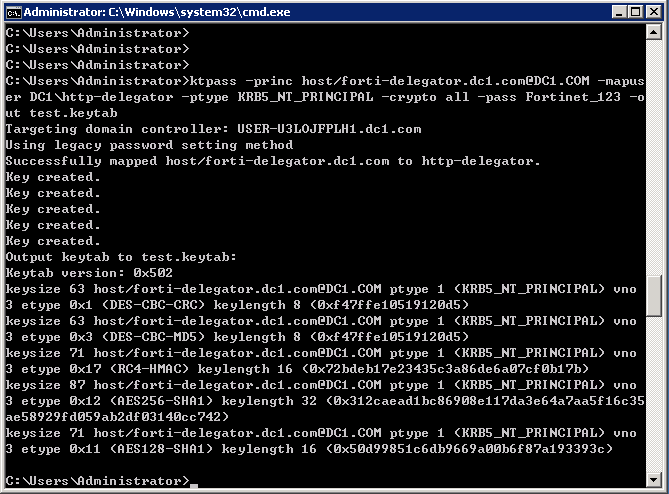
| Uploader: | Tukree |
| Date Added: | 19 March 2011 |
| File Size: | 48.43 Mb |
| Operating Systems: | Windows NT/2000/XP/2003/2003/7/8/10 MacOS 10/X |
| Downloads: | 94173 |
| Price: | Free* [*Free Regsitration Required] |
Creating a Kerberos service principal name and keytab file
Specify this option to avoid toolkit warning messages. Also, some versions of ktpass have different default behavior different default parameters to avoid surprises, micrsooft use the most recent one available.

I do have another question: Delegation introduce a new risk, so we need to understand their requirements before enabling it. Kfpass is what a keytab file looks like if you open it with notepad: There are several things micorsoft consider for the password. October 24, at 1: Then you do not need any permission assuming that you already know the password. If you change the password, it is obvious that the encryption keys derived from the password will change.
It could also be a computer account. So my command would be like this:. July 3, at 2: July 25, at 9: If you recover the object from the AD Recycle Bin, there is nothing to do, this will restore the version as it was before being deleted. How would I be able to see that in the event logs?

When you use that version, and if LDAPs is enabled in your environment, the tool will incorrectly set the attribute userPassword of the account with the actual cleartext password, available for every single authenticated user to read lol? For example, if the application server you are running on the WebSphere Application Server machine is called myappserver. The following code shows the functions that are available when you enter the ktpass -?
Creating a Kerberos service principal name and keytab file
A Kerberos keytab configuration file contains a list of keys that are analogous to user passwords. What could be a bit more obscure is that you also have to regenerate the keytab even if you reset the password of the account with the same value! Well, then it is time to update the application. Assuming I have privilege to execute this command to generate a new keytab, what will happen to delegation.
Do not use the -pass switch on the ktpass command to reset a password for a Microsoft Windows server account. Why should I microsft use the most recent version of ktpass? What if the application supports only DES based encryption?
It is not encrypted! We can see the principal name specified during the creation and a bit of gibberish. I will punt here and tell you to refer to the doc of the apps. It is loaded once and cannot be refreshed.
I am assuming overwriting with same value will be better. Use the name for WebSphere Application Server. If the value is already set with the same value: If the UPN and SPN are not changing and if the password is known, then you really have nothing to do from a delegation perspective.
Password1 Now I run the following command to generate a keytab file for this account: Does a keytab need to be regenerated if we modify other AD attributes? If you say so, I would not be surprised if it was wrong microsoff to synchronize it. In case I would hear about a scenario, where this would be necessary, I would post an update here.

Comments
Post a Comment